Filtering Spam, Malware & File Types
TEKRiSQ Mail Filtering comes as a package of inbound filtering:
Any email will first go through our mail filter before reaching your inbox, mitigating many threats and reducing the attack surface.
Most of the latest successful attempts have been through phishing emails or attachments, having a filter will block these attempts from reaching a user's inbox.
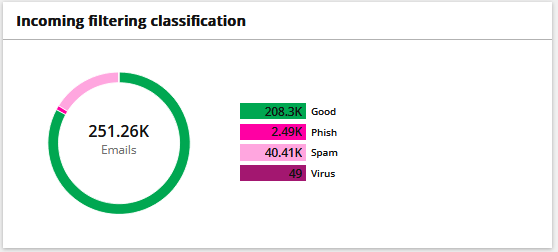
Not only that but we also provide the users a way to check their own emails with a portal:

Email Filtering Techniques
The techniques used in email filtering will determine how effectively mail is routed. An organization should consider what they want in an email filtering solution. A combination of the following techniques can help organizations achieve maximum effectiveness:
- Reputation-Based Email Filters: Attempts to stop spam or allow legitimate email by filtering out known spammers or approving trusted senders based on reputation databases. Reputation Block Lists (RBLs) are lists of domains, URLs, and IP addresses that have been analyzed and deemed as possible security threats. RBLs are one of the main ways organizations can use spam filtering for protection.
- Whitelisting: Provides organizations the ability to determine which senders they accept email from by adding them to a list.
- Blacklisting: Provides organizations the ability to determine which senders they want to block email from by adding them to a list.
- Anti-virus: Protects against new and existing viruses and other forms of malicious code using signature-based and non-signature-based technology.
- Content Analysis: Offers the ability to block an email based on the content of the message. For example, if a message contains certain words, the content filter can determine that it is a spam message. Another example is if the message contained an attachment and the organization doesn’t want to let it through. Another form of content filtering is Bayesian analysis. Bayesian analysis improves spam filtering by learning from each message it scans. The more messages are scanned, the greater the effectiveness of the analysis.
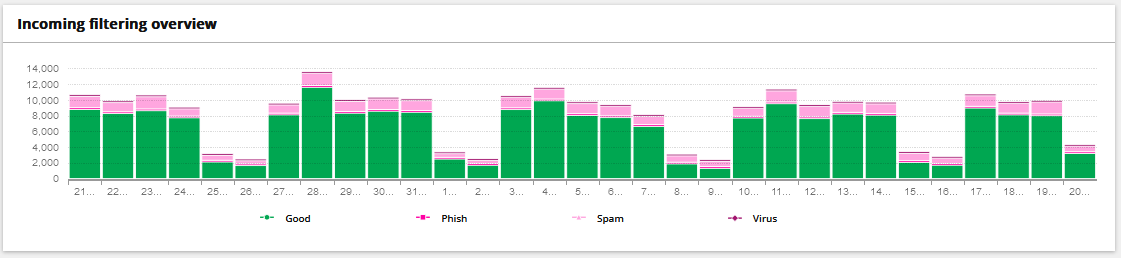
Using mail filtering, we can whitelist allowed emails to come through or blacklisting for any unwanted senders.
We can apply filtering rules to allow/block certain patterns of email content.
Deployment is easy, whether you have a G Suite domain or an O365 domain.


