
2022 Industry News in Review
The past year in cybersecurity was an uncommon one, filled with continual anticipation, but the
signature for the year may just be that there was no real signature event. There was no long-term panic
over the scope of vulnerabilities (such as log4j), no disastrous ransomware attack on infrastructure like
the Colonial Pipeline incident, no exotic malware, and no shocking information breaches or hacks like
we have seen in the past. And while there were surprising developments and incidents that had
potential for major fireworks. Overall it was a relatively low-key year. Despite the lack of blockbuster
incidents, there was plenty of cyber discomfort to share.
Much of the year was overshadowed by the conflict between Ukraine and Russia, with both countries
having robust offensive cyber capabilities. Given Russia’s strong cyberwarfare activities in past military
conflicts, it was widely anticipated that this intense “special operation” would be replete with major
newsworthy cyber incidents. Instead, it was largely muted, and many of the cybercrime organizations
either took sides or exposed internal rifts with members on both sides of the border, disrupting some of
the most capable malicious actors. That said, there was a notable increase in attacks against and from
both nations from what is otherwise considered “normal”—it just doesn’t appear from the outside as an
all-out offensive. This could be attributed to commendable efforts by cyber defenders for both nations—
otherwise we would see much more—but from a wide-angle view, attempts that may be taking place do
not appear to be having a significant impact.
The national elections in the United States, Italy, Northern Ireland, Brazil, Syria, India, and Philippines,
in addition to out-of-cycle political activity in the United Kingdom did not raise any more cyber
disruption than expected. It’s possible that the increased scrutiny around election security paired with
an increase in international cooperation among law enforcement were a significant deterrent, or these
events did not warrant the attention of the malicious cyber actors. With the cybersecurity industry
focusing so many resources on high-profile events, we can assume cybercriminals are satisfied with
the gains from their normal activities such as phishing and ransomware, and don’t feel the need to
overextend into high-profile attacks, in hopes of not drawing too much attention to themselves. It
seems likely that all of these factors play some role in that process.
Old tools and approaches seem to be working as well as they ever have. In fact, some of the threat
actors and criminal groups that had been believed to be defunct have rebranded, resurfaced, or
reorganized. Banking trojans such as Dridex enjoyed a resurgence this year, as did suspected
members of Evil Corp. Malware loaders that had been disrupted such as Emotet, ZLoader, and
Trickbot resurfaced and evolved into new configurations. Individuals formerly believed to be working for
one group emerged in other groups, sometimes raising speculation that they were contracting their
skills to multiple platforms or concern that new partnerships and organizations were emerging.
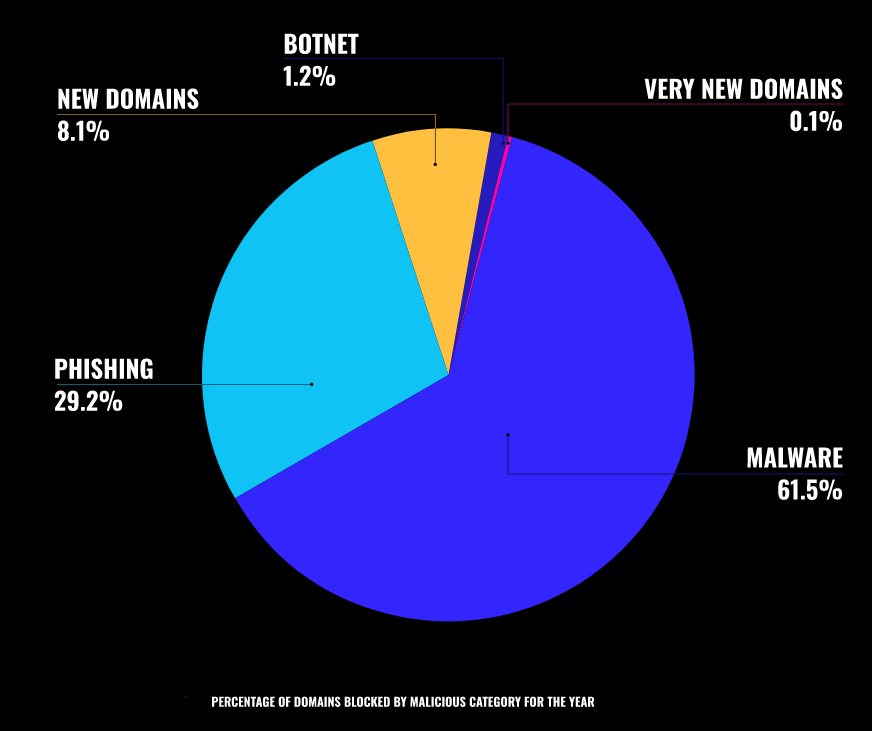
New Domains Will Never Stop Being Dangerous
This continues to be a critical truth. In fact, we believe this so strongly that after we looked at the data,
we added “very new domains” as an entirely new category to our product to better address the issue of
deceptive domains being created and used for incredibly short periods of time, often for malicious
purposes. Malicious websites are often leveraged within the first three to seven days of their lifespan.
In an effort to dial in on that threat more effectively, a set of constraints has been applied on a machine
learning module to catch domains that have never been seen before, and evaluate them for twenty-four
hours from their initial appearance in order to assess whether they may be used for malicious
purposes.

Subcontractors Should be Aware
Recent years have seen a number of very critical vulnerabilities
published, leaving many of even the best-defended networks
open to attack. The method an attacker will use is always going
to be the one that requires the least time, effort, and expense.
Subcontractors and small- to medium-sized businesses are
much softer targets than the main contractors that hire them,
and often the governing policies and standards utilized by these
smaller entities are not as robust as those used by larger
companies. As long as those less well-developed security
practices are able to provide privileged access to more secure
ones, they will always be the better target. Improved regulation
and stronger security requirements will be required from the top
to the bottom of the supply chain if this is ever going to improve,
and in the meantime subcontractors should do everything they
can to protect themselves and their assets.


